
Click any of the items in the Malicious programs and exploits panel, or the Malicious programs and exploits section in the Classification of all programs run and scanned panel, to view a list of all the threats found on the computers protected with Adaptive Defense 360.
Select Exploits.
The default option is Malicious programs.

The top of the window displays a search tool:

Filter (1) restricts the search indicated in text box (2):
Computer: The search string will be applied to the computer name.
Compromised program: The search string will be applied to the program compromised by the exploit.
Date: The search string will be applied to the date of detection.
MD5: Hash value identifying the file.
Filter (3) shows those exploits that match the selected criteria. Risk: The risk depends on the action taken on the exploit.
The compromised computer is or has been at risk:

The compromised computer hasn't been at risk:

Action |
Description |
Risk |
| Allowed by the user | The exploit was identified by Adaptive Defense 360 but the end user decided to let it run. |  |
| Allowed by the administrator | The exploit was identified by Adaptive Defense 360, but the administrator decided to let it run. |  |
| Blocked (immediately) | The exploit was identified by Adaptive Defense 360, which blocked it immediately after detecting it. |  |
| Blocked after the process was ended. | The exploit was identified by Adaptive Defense 360, which blocked it after the compromised process was ended. | 
The time that passes between detecting the exploit and ending the compromised process is a period in which your network is at risk. |
| Detected. Pending restart. | The computer must be restarted to finish blocking the exploit successfully. Make sure the computer is restarted as soon as possible. | 
The time that passes between detecting the exploit and restarting the computer is a period in which your network is at risk. |
The table fields are as follows:
Computer: Computer where the detection took place.
Compromised program: Program compromised by the detected exploit.
Action: Action taken on the exploit (Allowed by the user, Allowed by the administrator, Blocked (immediately), Blocked after the process was ended, Detected. Pending restart).
Risk:
Indicates the degree of risk ( /
/ )
based on the action taken on the exploit.
)
based on the action taken on the exploit.
Date: Date when the exploit was detected on the computer.
Click the arrow after the Date column to display additional information about the exploit.
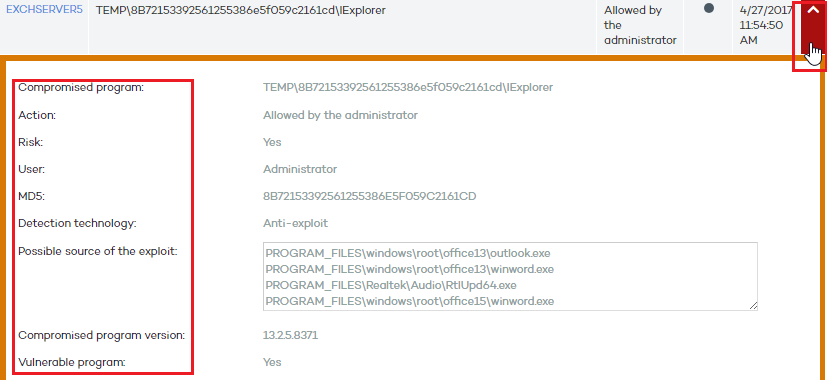
The available information is as follows:
Path of the compromised program
Risk
User: Logged-in user
MD5: MD5 hash value identifying the file.
Detection technology: Anti-Exploit
Last accessed URLs: If the exploit originated from a Web page
Possible source of the exploit: If the exploit originated from a file, a list of potential source files will be displayed
Compromised program version: This field may be blank
Vulnerable program (Yes/No): This field may be blank
Finally, you can view the exploit's life cycle on the computer and access the corresponding activity graph.
Click the  icon in the
Action column to display the command
line and execution parameters used in the attack.
You can copy this data by selecting the text and using the Copy-Paste
option in the context (right-click) menu.
icon in the
Action column to display the command
line and execution parameters used in the attack.
You can copy this data by selecting the text and using the Copy-Paste
option in the context (right-click) menu.
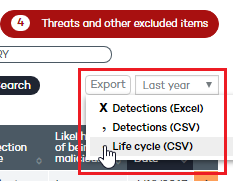
You can also export this information. Use the option to export the blocked item's life cycle to .CSV format. You'll find it in the upper-right corner of the window.
To exclude an exploit, go to the Exclusions section in the Advanced protection settings of the relevant profile. This section will allow you to exclude the compromised application from all the scans performed on those computers to which the relevant profile is applied.
Note that the Disinfect computer option is not available in the Anti-exploit protection.