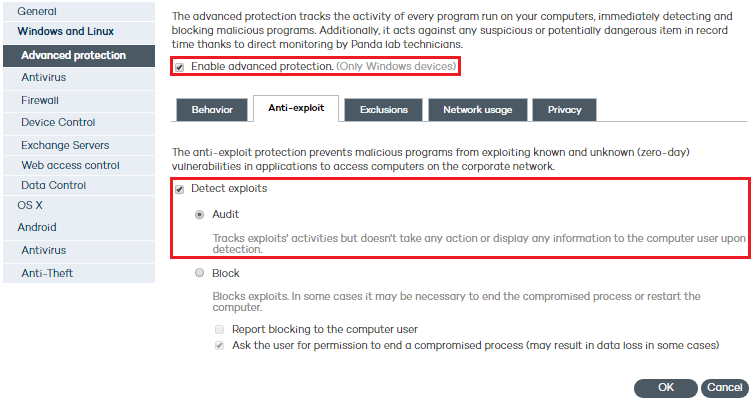
Once you have enabled the advanced protection and the anti-exploit protection, the actions that can be taken on exploits are:
If you select Audit, Adaptive Defense 360 will report all exploit detections in the Web console, but won't take any actions against them or notify the compromised user.

These notifications can be sent via email to the administrator, based on the email alert settings configured in the Preferences section (accessible through the General settings button).
This option is not recommended. It is better to set the protection to report exploit detections AND take action on them for it to be really effective.
You can change the default behavior of the anti-exploit protection to apply remediation measures and stop attackers from continuing to compromise the target application, and, from there, the entire network. Follow the steps below:
Select the Detect exploits checkbox.
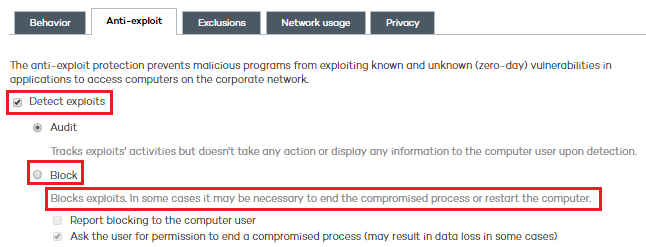
Select Block.
The protection will try to block the attack immediately upon detection without end user intervention. In some cases it may be necessary to end the compromised process or restart the computer.
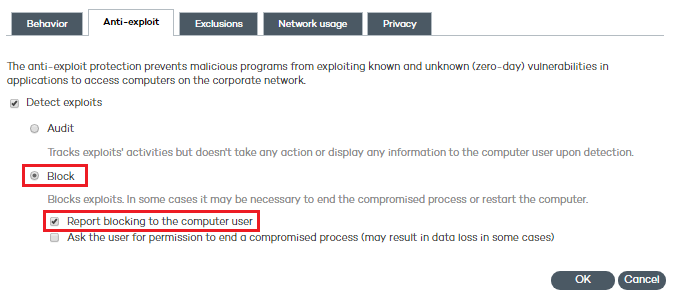
Select this checkbox if you want the user of the compromised computer to be informed every time an exploit is blocked.
Select this checkbox if you want to ask the user of the compromised computer for permission before ending a compromised process.
This will allow the user to, for example, save their work or critical information before the compromised process is ended or their computer is restarted.
 Important:
Important:
The exploit neutralization and removal process doesn't end until the compromised process is ended or the computer is restarted. It is important to bear in mind that exploits are hosted in memory, where they continue to run malicious code. Therefore, until the compromised process is ended or the computer is restarted, the exploit won't be successfully blocked.
Related topics
Configuring the advanced protection
Examples of vulnerability exploit techniques