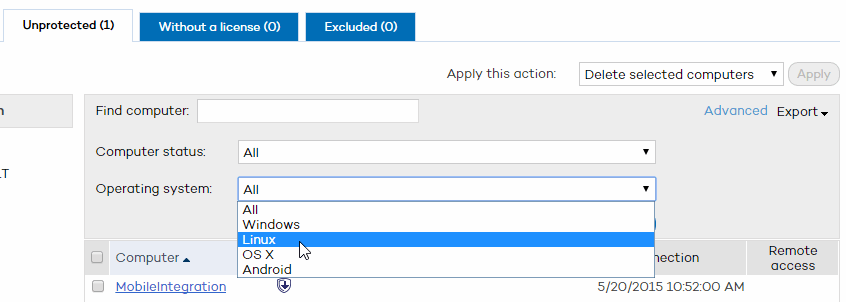
The Computers window displays a list of all the unprotected computers on your network.
A computer will appear as unprotected when the protection is being installed/uninstalled, when there has been an error installing/uninstalling the protection, or when the computer has been discovered through a search.
Additionally, the group tree on the left-hand side of the window will let you move through the different group levels and see the computers included in each group.
When it comes to searching for unprotected computers, you can enter the name of a computer in the Find computer box and click Find.
You can also use the Computer status menu to filter computers according to their status:

Select a status and click Find.
The search results are presented in five columns:
The Computer column shows the list of the unprotected computers in the organization, presented either by their name or by their IP address. If the name of a computer is not known, the word Unknown will be displayed.
The Status column shows the status of the protection installed on the computer through a series of icons. Click Key to see what each icon represents.
The Details column describes the reason for the computer status. For example, if the status is Install error, the Details column will display the error code. Another example: If the Status column shows No protection, the Details column will show Protection uninstalled.
Last connection. Shows the date and time of the last connection with the computer.
Remote
access. If
the following icon is displayed
 ,
it indicates that the computer has Panda Remote Control installed.
Click it to open a remote desktop connection or select a troubleshooting
action. If the column displays the following icon
,
it indicates that the computer has Panda Remote Control installed.
Click it to open a remote desktop connection or select a troubleshooting
action. If the column displays the following icon  , it means that the computer
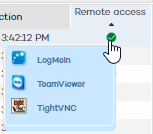
has a different remote access tool installed. If it's only one, click
the icon to access it. Enter the relevant credentials and access the
computer.
, it means that the computer
has a different remote access tool installed. If it's only one, click
the icon to access it. Enter the relevant credentials and access the
computer.
However, if the computer has several remote access tools installed, placing the mouse pointer over the icon will display all of them. Select one to access the computer remotely.
OS X computers will appear as unprotected when discovered through a computer search launched from the Web console.