Click any of the items in the Potentially Unwanted Programs panel to view a list of the threats found on the computers protected with Adaptive Defense 360.
The information on the list will be already filtered based on the counter that you clicked (Accessed data, Made external connections, etc.).
At the top of the window there is a search tool:

Filter (1) restricts the search indicated in the text box (2) to its right:
Computer: The search string will be applied to the computer name.
Name: The search string will be applied to the PUP name.
Date: The search string will be applied to the date of detection.
MD5: MD5 hash value identifying the file.
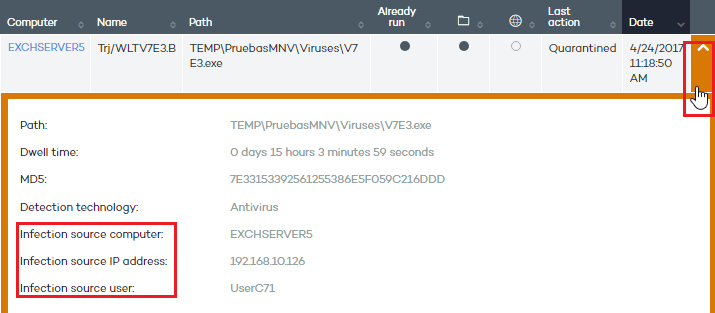
Infection source: The search string will be applied to the computer that the infection originated from. The text string will be searched in the following fields: Infection source computer, Infection source computer IP address, and Infection source user.
Filter (3) shows the potentially unwanted programs that match the selected criteria:
Not run: PUP detected by the protection against vulnerabilities.
Run: The PUP was run and the computer is infected.
Access to data files: The PUP accessed the disk to collect information from the computer, or to create the files and resources necessary for its execution.
Communications: The PUP opened sockets for communicating with other computers, including localhost.
Blocked: PUP identified by Adaptive Defense 360 and prevented from running.
Quarantined: The PUP could not be disinfected and was sent to quarantine.
Deleted
Disinfected: The PUP was disinfected by the antivirus.
Allowed by the user: PUP identified by Adaptive Defense 360 and allowed to run by the user.
The table fields are as follows:
Computer: Computer where the detection took place.
Name: PUP name.
Path: Full path to the PUP file.
Already run: The PUP has been run.
Accessed data: The PUP has accessed files located on the user's computer.
Made external connections: The PUP has communicated with remote computers to send or receive data.
Last action: Action taken on the PUP (block, allow, quarantine, delete, disinfect, allow by the user, etc.).
Risk: The risk will be high, medium or low, depending on whether the PUP was actually run, accessed data or and/or has communicated with external computers, and its activity.
Date: Date when the PUP was detected on the computer.
Click the arrow after the Date column to display additional information about the item, for example, detection technology, infection source user and IP address, as well as other details regarding the item's life cycle and the number of times it has been seen on the network.
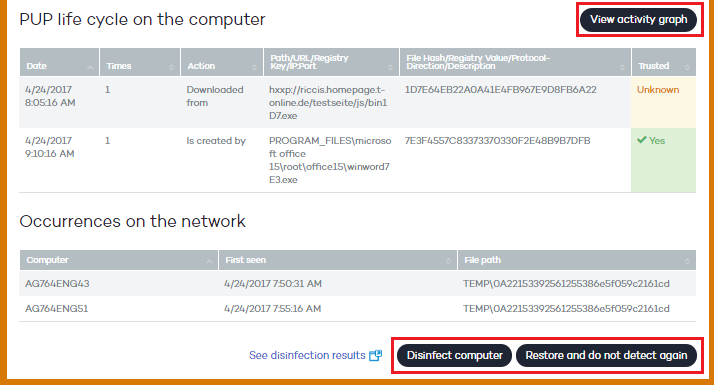
Also, this panel will allow you to disinfect the computer, restore the item so that it's never detected again, and use the activity graph to view a graphical representation of the actions performed by the threat.
Click the  icon in the
Action column to display the command
line and execution parameters used in the attack.
You can copy this data by selecting the text and using the Copy-Paste
option in the context (right-click) menu.
icon in the
Action column to display the command
line and execution parameters used in the attack.
You can copy this data by selecting the text and using the Copy-Paste
option in the context (right-click) menu.
You can also export this information. Use the option to export the PUP life cycle to .CSV format. You'll find it in the upper-right corner of the window.