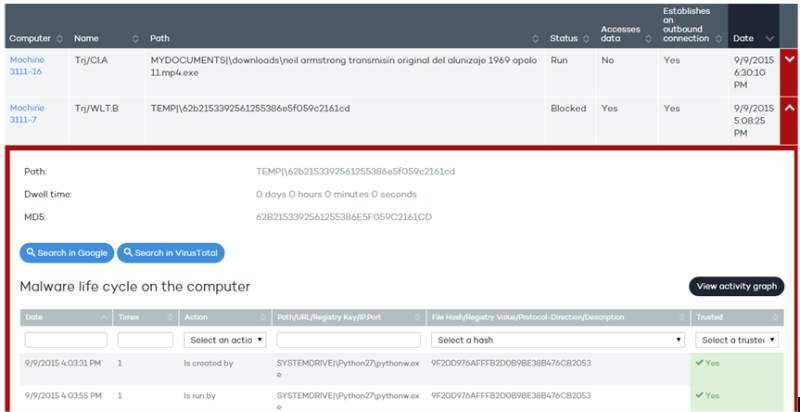
The Status window lets you access different lists of threats detected on the network by clicking the panels available in the Activity section. Click any of the threats to obtain a table with detailed information about its activity.

The fields included to generally describe a threat are:
MD5: Adaptive Defense 360 shows the malware hash for subsequent checking in VirusTotal or Google.
Malware path: Path of the executable that contains the malware.
Dwell time: Time that the threat has remained in the system.
Malware life cycle on the computer: This is a table that details each of the actions triggered by the threat.
Additionally, there are two buttons to search for further information on the Internet using Google and the VirusTotal website.
This table includes only the most relevant events, because the amount of actions triggered by a process is so high that it would prevent the extraction of useful information for a forensic analysis.
The table content is initially sorted by date, making it easier to follow the development of the threat.
The fields included in the action table are detailed below:
Date: Date of the action.
Times: Number of times the action was executed. A single action executed several times consecutively only appears once in the list of actions.
Action: Action taken.
Path/URL/Registry key/IP:port: Action entity. It can contain the following values depending on the action type:
Registry key: For all actions that involve modifying the Windows registry
IP:port: For all actions that involve communicating with a local or remote computer
Path: For all actions that involve access to the computer hard disk
URL: For all actions that involve access to a URL
File Hash/Registry Value/Protocol-Direction/Description: This field complements the entity. It can contain the following values depending on the action type:
File Hash: For all actions that involve access to a file
Registry Value: For all actions that involve access to the registry
Protocol-Direction: For all actions that involve communicating with a local or remote computer. The possible values are:
TCP
UDP
Bidirectional
Unknown
Description
Trusted: The file is digitally signed
The table header contains a series of filters to help you locate the actions of most interest in the list.
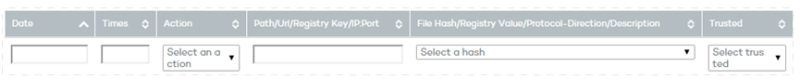
Some fields allow you enter text while others are drop-down menus. The text searches are flexible and do not require the use of wildcards to search within the text string.
Related topics