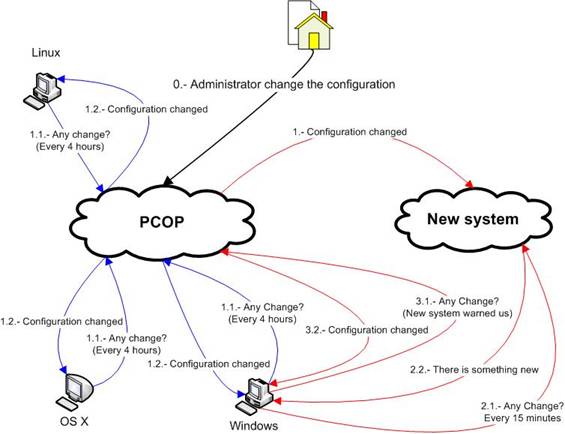
In previous versions of Endpoint Protection, computers contacted the server every 4 hours to see if there had been any configuration changes. This means that it could take up to 4 hours for any change made in the Web-based administration console to be applied on computers.
From version 7.0 a new system has been implemented that checks for configuration changes every 15 minutes. For this new system to work, computers must have an Internet connection, either direct or through a proxy server. It won't work if computers connect to the Internet through another agent (either configured as a static or dynamic proxy).
This new system only works with Windows computers, it doesn't apply to Linux or OS X computers.
This new communications system has not replaced the old one, but rather complements it. Both systems coexist so that if the new system fails, the old system takes over, meaning that it will take a maximum of 4 hours for any configuration change to be applied on computers.
The old system worked as follows:
The administrator made a configuration change in the Web console.
Each computer contacted the server every 4 hours to check if there had been any configuration changes.
If there was a configuration change, the server delivered it to the computer, which applied it.
The new system works as follows:
The administrator makes a configuration change in the Web console.
The server informs the new communications system, which in turn notifies affected computers that a configuration change has been made.
The affected computers are as follows:
If the administrator changes a profile's configuration, the change will affect every computer in the groups that have that profile assigned to them.
If the administrator changes a computer's configuration, the change will be notified to every computer in the same group.
Each computer checks for new notifications every 15 minutes. If there is a new notification:
The computer asks the Endpoint Protection server for the new configuration policies.
The server delivers the policies to the computer, which applies them.
The diagram below shows how both systems work:

The protocol used by the new communications system is HTTPS. To use it, computers must access two different domains:
Computers check periodically if they have access to the communications system. More precisely, this check takes place every time the agent service is started, upon querying the communications system for the first time, and every 24 hours as long as the system is operative.
Computers contact the communications system every 15 minutes to check if there are any new notifications.
For more information about the domains to be accessed by the computers, refer to the following article: http://www.pandasecurity.com/enterprise/support/card?id=50022