Users can choose the path where they want to install the product, however, the default installation path is:
%allusersprofile%\Datos de programa\Panda Security\Panda Endpoint Protection\Quarantine

![]() EndPoint
Protection installation path. This contains
the files needed for EndPoint Protection to operate.
EndPoint
Protection installation path. This contains
the files needed for EndPoint Protection to operate.
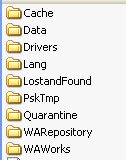
Cache: Contains the local signature files.
Data: Contains the behavior analysis technology data files.
Drivers: Contains the binaries used to install/uninstall the units.
NNSNahs: Binaries used to install the firewall intermediate driver.
PSINDvct: Binaries used to installthe Device Control technology driver.
Lang: Contains the dictionaries with the strings in the various languages.
LostandFound: Contains the items restored from quarantine when they’ve been moved by the email protection or when they couldn’t be restored to the original path.
Quarantine: Contains quarantined items.
PskTmp: Temporary configuration files created during the scan.

Panda Security: Key in HKEY_LOCAL_MACHINE\Software\Panda Security that contains the protection keys and values.
AdminIE\Protections: Key that contains the WAC value indicating where the client is installed.
Nano Av\Boot: Kept to maintain compatibility with previous versions. Not currently used.
Nano AV\ModAV: Kept to maintain compatibility with previous versions. Not currently used.
Nano Av\Live: Contains the DownloadFolder value indicating the client’s downloads folder
Nano Av\Panda Main Service: Contains the plug-in loading values for the antivirus main module.
Nano Av\Setup: Contains the protection installation path.
Panda Service Host: Contains the plugins loaded in the service: update system, antivirus main system, engine, file and process interception system, device control configuration system, firewall.
Panda Software\Setup: Product information (name, version, ID, installation path, etc.)
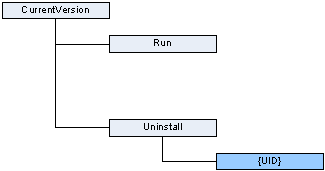
This section deals with the registry entries Panda EndPoint Protectioncreates in the “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion” key.
![]() HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
![]() System
key that indicates the path of the applications launched at the beginning.
System
key that indicates the path of the applications launched at the beginning.

![]() System
key with information about uninstallers of products installed on the system.
System
key with information about uninstallers of products installed on the system.
Panda Universal Agent Endpoint: Key with the information needed to uninstall the product.

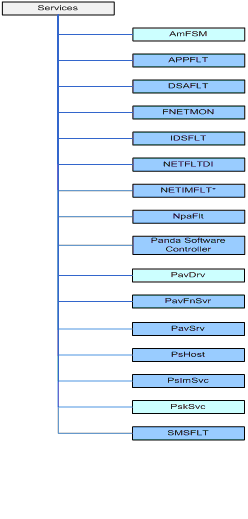
![]() HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
NNSALPC: Firewall driver
NNSHTTP: Firewall driver
NNSIDS: Firewall driver
NNSNAHS: Firewall driver
NNSPICC: Firewall driver
NNSPIHS: Firewall driver
NNSPOP3: Firewall driver
NNSPROT: Firewall driver
NNSPRV: Firewall driver
NNSSMTP: Firewall driver
NNSSTRM: Firewall driver
NNSTLSC: Firewall driver
PRKPAVPROC: Driver used in rookit scanning.
PSBOOT.SYS: Driver for operations at boot.
PSINAflt: Intercepting filter.
PSINDvct: Device Control driver.
DVCTPROV.sys: Device Control driver.
PSINFile: File intercepting driver.
PSINKNC: Kernel intercepting driver.
PSINProc: Process intercepting driver.
PSINProt: Protection driver (shield, KRE).
PSKMAD: Memory scanner driver.
PSUAService: Task control and management service in sessions.
NanoServiceMain: Client’s main service for all protection modules.
CLOUDUPDATEREX: Upgrade tasks service.
Apart from the services mentioned above, the following processes can be run on the system:
bspatch.exe
Process used to patch signature files.
PAV2WSC.exe
Process used to update the antivirus status in Windows Security Center.
PSANCU.exe
Process used to perform configuration tasks during client installation and upgrades.
PSINanoRun.exe
Process used to install and upgrade the client.
PSNCSysAction.exe
Process used to enable/disable the firewall’s NNSNahs intermediate driver.
PSUAMain.exe
Traybar process.
PSUNMain.exe
Client interface process.
Setup.exe
Installation and upgrade tasks process.
WAScanner.exe
Process that manages the background scanning tasks configured from the Web console.