Click the different panels in the Activity section to display reports and detailed lists of the malware and software under analysis found on the customer's network.
The purpose of these lists is to provide administrators with the necessary information to find the source of a problem, assess the severity of an incident and, if required, take the necessary remediation measures and update the company's security policies.
These lists also allow administrators to add exclusions and unblock currently blocked items under analysis. See later in this document for more information about the exclusion and unblock operations supported by the solution.
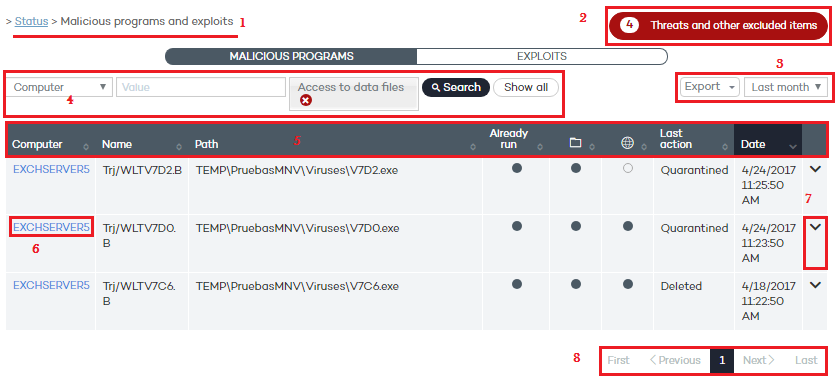
All of these lists have the same structure:

List name.
Number of excluded items: files in the process of being classified, blocked items, and items classified as malware/PUP by Adaptive Defense 360 allowed to run by the administrator.
Time interval drop-down menu and list export tool. The time period menu allows the administrator to apply the following time filters to the list: last 24 hours, last day, and last month. The export tool allows the administrator to export the list to Excel and .CSV format, and the life cycle to .CSV format.
Filter tool. Each list incorporates its own filters based on the data it contains. These are explained in the relevant sections.
You can sort the data in the tables by clicking the column headers.
Click a computer's name for extended information.
IP address: The computer's IP address.
Installation date: Date when the agent was installed on the computer.
Last connection: Last time the agent connected to the Adaptive Defense 360 server.
Operating system.
Group: Group to which the computer belongs.
Protection mode: Advanced protection mode currently configured in the computer (Audit, Hardening, Lock).
Extended information about the actions taken by the malware. Refer to chapter Forensic analysis for more information about the actions performed by the detected malware. Refer to chapter Remediation actions for more information about the remediation tools provided by Adaptive Defense 360.
Pagination controls for easier navigation.