Here you can configure aspects related to the installation of the protection on your computers, as well as the connection of those computers to the Internet and to the Adaptive Defense 360 servers. You can also configure options related to the suspicious file quarantine.
Specify in which directory you want to install the protection. Adaptive Defense 360 shows a default path, which you can change if you want.
Automatically uninstall other security products:
You can specify if you want Adaptive Defense 360 to uninstall any existing third-party security products from your computers, or if you prefer both products to coexist.
Bear in mind that if you choose to uninstall all existing third-party security software on a specific configuration profile, every computer that has that profile assigned will have its protection removed as soon as it receives the new configuration.
Click here for a complete list of the antivirus solutions that Adaptive Defense 360 uninstalls automatically.
Administrators can disable scans with Collective Intelligence. We advise that you keep this option enabled if you want to benefit from the detection power provided by Collective Intelligence.
Establish how often you want computers to send information to the Adaptive Defense 360 servers about the status of the protection installed. This must be a value between 12 and 24 hours.
Centralize server communication through the following computer: Specify the computer through which you want to centralize all connections to the Adaptive Defense 360 server.
To do that, select the relevant checkbox and click Select. In the Select computer window, choose a computer or search for it using the Find button. Then click OK.
Lets you indicate the path on the user's computer where detected suspicious items will be temporarily stored. By default, these files will be stored in the Quarantine folder in the installation directory.

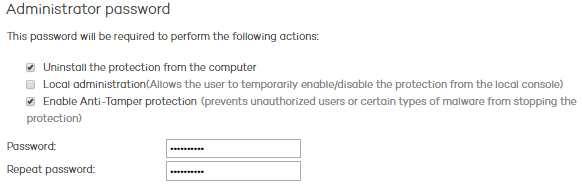
The administrator password allows you to uninstall and configure the local protection in administrator mode. That is, it allows you to uninstall Adaptive Defense 360 from the network computers, or allow end users themselves to enable or disable their protection from the Adaptive Defense 360 local console.
These options are not mutually exclusive, so you can select both at the same time.
This section also allows you to enable the new Anti-Tamper protection, which prevents unauthorized users and certain types of malware from stopping the protection installed on the network.