The Peer-to-Peer (or 'rumor') functionality reduces Internet bandwidth usage, as those computers that have already updated a file from the Internet then share the update with the other connected computers. This prevents saturating Internet connections.
The P2P functionality is very useful for deploying Adaptive Defense 360 and downloading the installation program. As soon as one of the computers downloads the Adaptive Defense 360 installation program from the Internet, the others are informed by their communications agent.
Then, instead of accessing the Internet, they get the installation program directly from the computer that downloaded it and install the protection.
This functionality is also very useful when updating the protection engine and the signature files, and is implemented in the two local processes that need to download files from the Internet: WalUpd and WalUpg.
The P2P functionality is enabled in the configuration files walupd.ini and walupg.ini, located in the InstallDir folder in the Adaptive Defense 360 installation directory:
WALUPD.ini
[GENERAL]
UPDATE_FROM_LOCAL_NETWORK=1
WALUPG.ini
[GENERAL]
UPGRADE_FROM_LOCAL_NETWORK=1
The P2P functionality works independently in each of these local processes. It may be enabled in one, but not in the other.
As soon as a computer has updated its signature files or any protection (or the agent itself), it sends a broadcast message with the information about the files that it has to the other computers on the network.
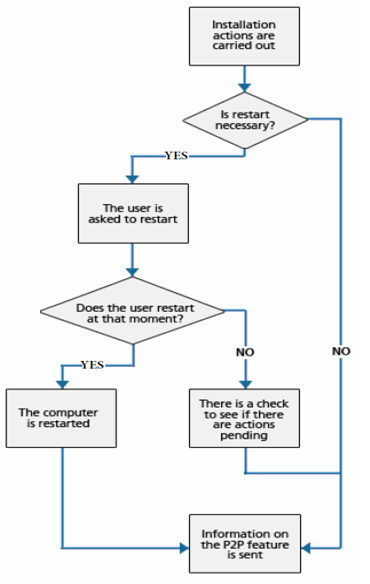
As for the information for the WALUpg process, if a restart is necessary after installing/upgrading the protection, and the user chooses to restart later, the information transmitted via the P2P functionality will be sent immediately instead of waiting for the restart.
The process is illustrated in the following diagram:

The computers save the information they receive, in order to use it when required. If a computer needs a file, it will first check whether another computer on the network has it before downloading it from the Internet. If so, it will request the file from the other computer. The file will be received asynchronously and there is a maximum time that must elapse before retrying.
Once the computer that requested a file receives it, it will continue with the update or upgrade process.