Popular devices like USB flash drives, CD/DVD readers, imaging and Bluetooth devices, modems and smartphones can become a gateway for infections.
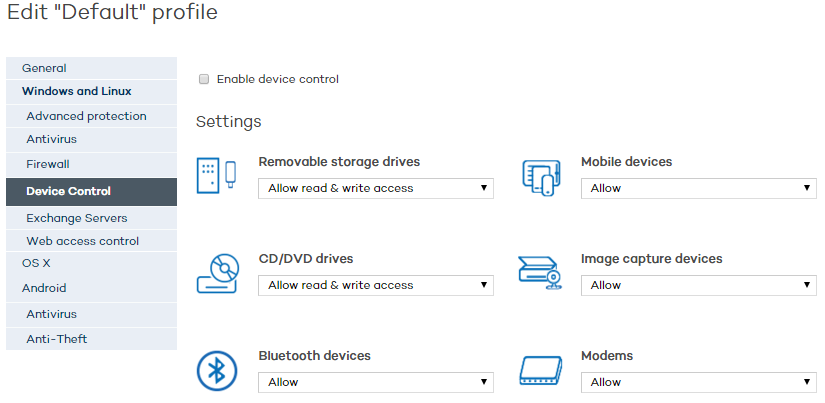
The device control settings allow you to configure the device control protection for the profile you are creating. Select the device or devices you want to authorize or block and specify their usage.
Follow the steps below to enable the device control feature:
Select the Enable device control checkbox.
In the relevant menu, select the authorization level for each device type.
In the case of USB flash drives and CD/DVD drives, you can choose among Block, Allow read access or Allow read & write access.
The options available for Bluetooth and imaging devices, USB modems and smartphones are Allow and Block.

Sometimes, you may need to block a certain category of devices but allow the use of some specific devices belonging to that category. In that case you can create a whitelist, that is, a list of devices that will be allowed despite belonging to an unauthorized category.
Adaptive Defense 360 shows a list of all the devices connected to each computer. Click Add in the Allowed devices section to display the list, and select the devices that you want to exclude from the general blocking options configured.
Once you have finished configuring your list of allowed devices, you can export it to a text file. You can also do the opposite, that is, create a text file with the devices that you want to allow, and import it to the Adaptive Defense 360 Web console.
Use the Export and Import buttons to export and import already configured exclusion lists.
Every time that Adaptive Defense 360 detects an unauthorized device, it blocks it and logs the incident in the Detection details section.
To access the Detection details section, go to Status > Detection origin > Detection details > Detected threats > Devices blocked.
There you'll see a button called Allow this device.