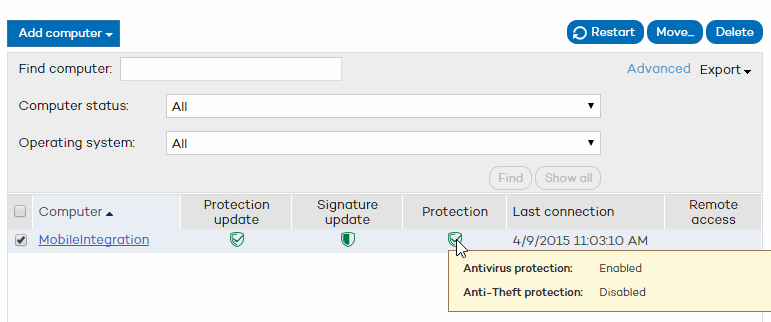
The list of protected computers displayed in the Computers tab lets you know the status of the protection installed on all the computers on your network.
Bear the following in mind:
Linux computers. The protection for Linux computers allows for on-demand and scheduled scans only.
OS X computers. The protection for OS X computers provides permanent file protection only. Click here for more information.
Android devices. The protection for Android devices provides permanent antivirus protection and anti-theft protection (only available if you have licenses).

Select, from the group tree, the group or subgroup that you want to explore.
Select All to see all computers, regardless of the group/subgroup they are in.
The number of computers that you see will depend on the permissions that you have. Refer to the Types of permissions section.
To add a computer, click Add. Refer to the Installation methods according to the operating system section for information about how to install the protection on computers depending on their operating system.
You can display all protected computers by using the Show all button, or click the Advanced option to search for computers depending on the status of their protection or their operating system:
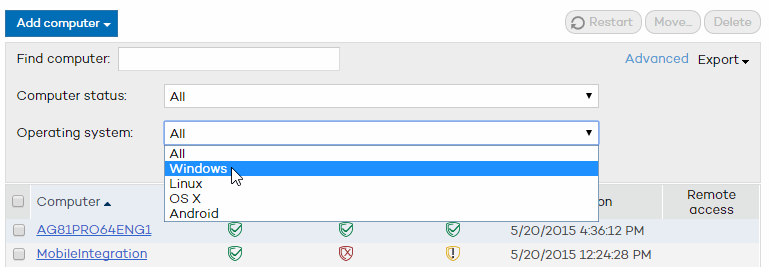
In the case of OS X computers, the information in the Protection column will only refer to the file protection: enabled, disabled or with errors.
In the case of Linux computers, the Protection column will show an icon indicating that the protection is OK.
The search tool is also very useful for finding out which computers do not have an up-to-date version of the signature file, or getting a list of those computers which, for whatever reason, have not connected to the server in the last 72 hours.
Select a status from the Computer status drop-down menu and click Find.
The search results are presented in five columns:
The Computer column shows the list of protected computers, presented either by their name or by their IP address. If different computers have the same name and IP address, they will be displayed as different computers in the Web console provided that their MAC address and administration agent identifier are different.
If you want to change the way they are presented, go to the Preferences section at the top of the Web console.

The Protection update, Signature update, and Protection columns use a series of icons to indicate the update status of the protection and its general situation. Place the mouse pointer over each icon to view this information.
In Last connection you can see the exact date and time at which the computer last connected to the update server.
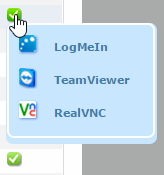
Remote access. If an icon is displayed in this column, it means that the computer has at least one remote access tool installed. If the computer has only one tool installed, click the icon to access it. Enter the relevant credentials and access the computer.

Bear in mind that the remote access feature is only available for Windows computers.
If the computer has multiple tools installed, place the mouse pointer over the icon to display all of them. Select one to access the computer remotely.
If you place the mouse pointer over a computer's name, a yellow tag will be displayed with the following information:
IP address.
Full path of the group the computer belongs to.
Operating system installed on the computer.
Protection installation date.
Comment associated with the computer.
Other information.