In order to improve monitoring of the protection installed on computers, lets administrators search for unprotected computers.
Administrators can even do this remotely, seeing at any time which computers are protected or unprotected, from a location outside the network.
It is not possible to search for unprotected computers from a Linux or OS X computer.
It is not possible to simultaneously search for unprotected computers and run remote uninstallation tasks. For more information, refer to the Incompatibility between remote management tasks section.
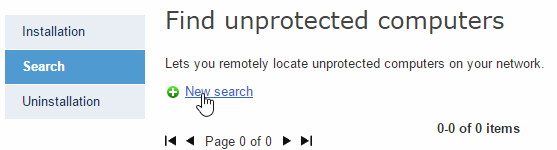
In the main console window, click Installation. Then, select Search in the menu on the left. This will take you to the Find unprotected computers window.
To create a new search task, click New search.

In the Edit search window, use the Select button to choose the computer that will perform the search.
The scope of the search will be defined depending on whether you choose the subnet of the computer performing the search, certain IP address ranges or certain domains.
The computer performing the search must meet a series of requirements.
Searches created are listed in the Find unprotected computers window, from where you can also remove search tasks, using the Delete button.
Tasks with the status Starting or In progress cannot be deleted.
Information is organized into the following columns:
Name: This shows the name given to the search when created.
Status: The status icons indicate the status of the search task. Click Key to see what each icon represents.
Discovered: This details the number of unprotected computers discovered.
Date created: Date the search task was created.
Created by: User that created the task.
Depending on your permissions, you will be able to create, view, or delete search tasks. For more information, refer to the Types of permissions section.
Click the name of one of the search tasks displayed in the Find unprotected computers window to go to the Search results window. This will display all the unprotected computers that have been discovered after running the relevant search.
In addition to the name of the search, its start and end dates and its status, the window will report any errors that might have occurred in the search process.
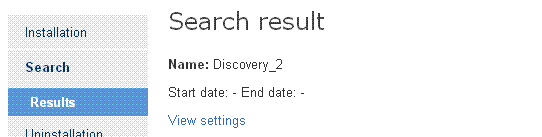
If the status of a search task is On hold, the start date will display a hyphen (-). The same applies to the end date if the task has not finished.
To view the settings of a search task, use the View settings link.