The protection provided by is designed to be installed and distributed across your IT network. Therefore, the protection to be installed will vary depending on the computers to protect and your specific security needs.
provides cross-platform protection that allows you to protect your Windows, Linux and OS X workstations and servers.
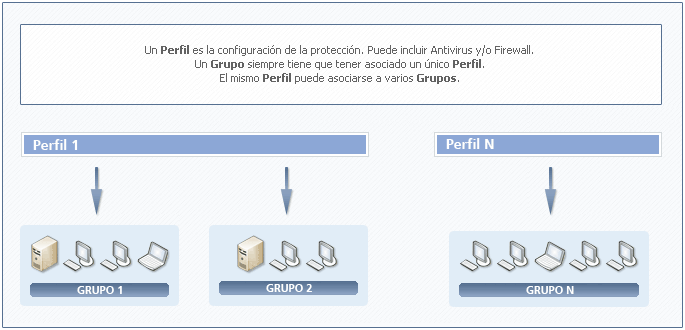
You can configure the protection before or after installation. To do this, you have to create a profile and then assign it to a group or groups of computers.
IMPORTANT: This Help file describes how to configure the various protection modules available when creating a profile from scratch (Settings / Profiles / Add profile /...). However, you can also edit the protection settings of an existing profile at any time. To do this, go to Settings / Profiles / Profile name, and change the relevant settings in the Edit profile window.
In this Help file, the configuration process is explained as a step prior to installing the protection on the computers.

When assigning profiles to the groups created, there are several options: one single profile applied to several groups, each group with a different profile, or just one profile and one group.
When you create a profile you configure the way that the protection will work for this specific profile, i.e, you determine which types of scans are carried out on which elements, and how often the protection is updated.
Before starting to install the protection, you can create and configure the profiles you need. Then, create groups of computers and assign the profiles to them, so that each group will have a specific protection profile.
If you want, you can install the protection on your computers with the default configuration provided by .