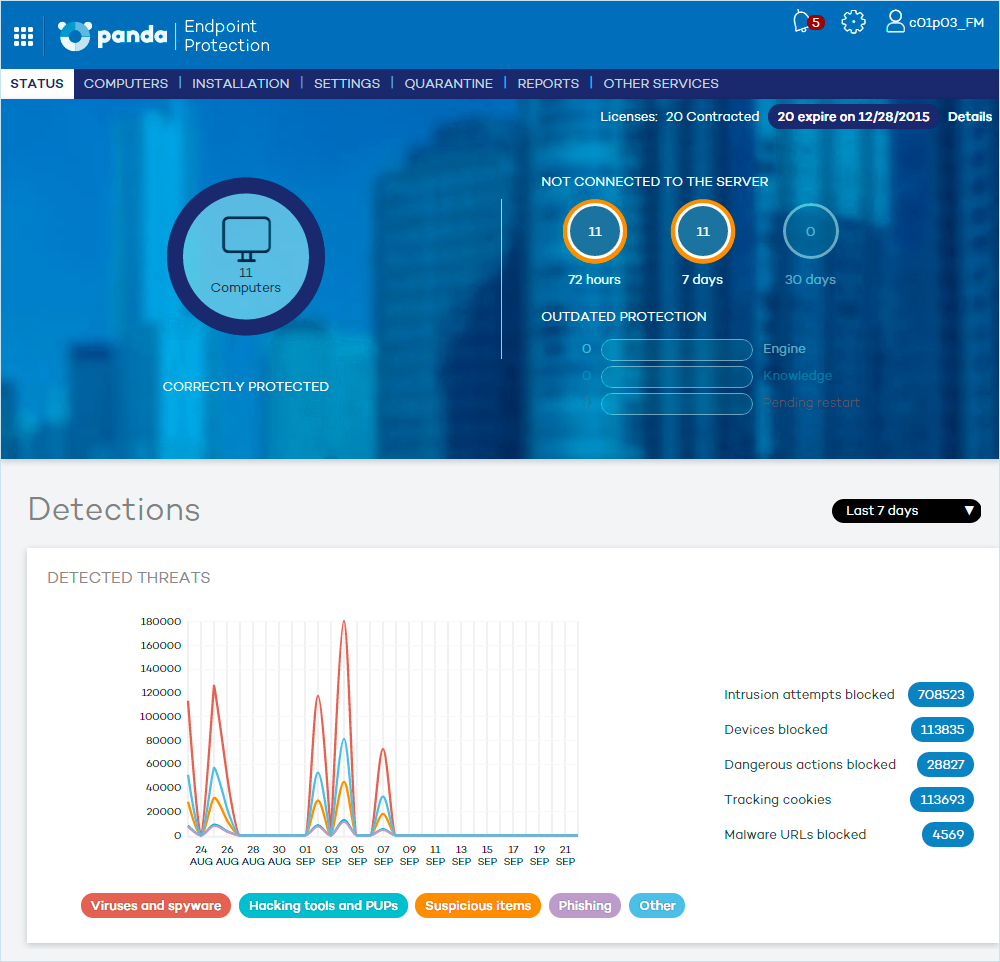
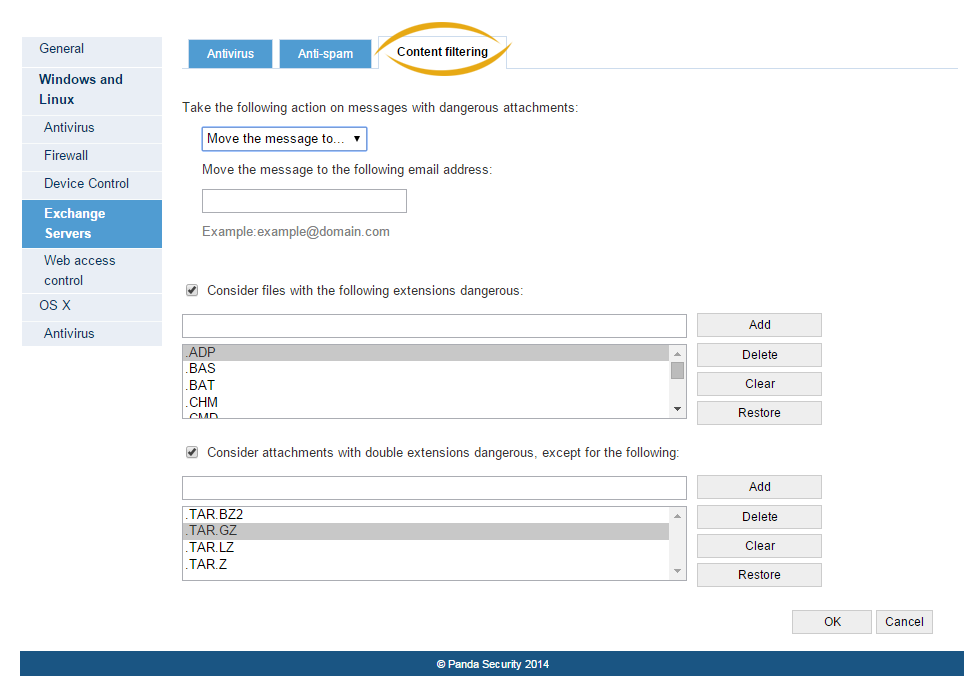
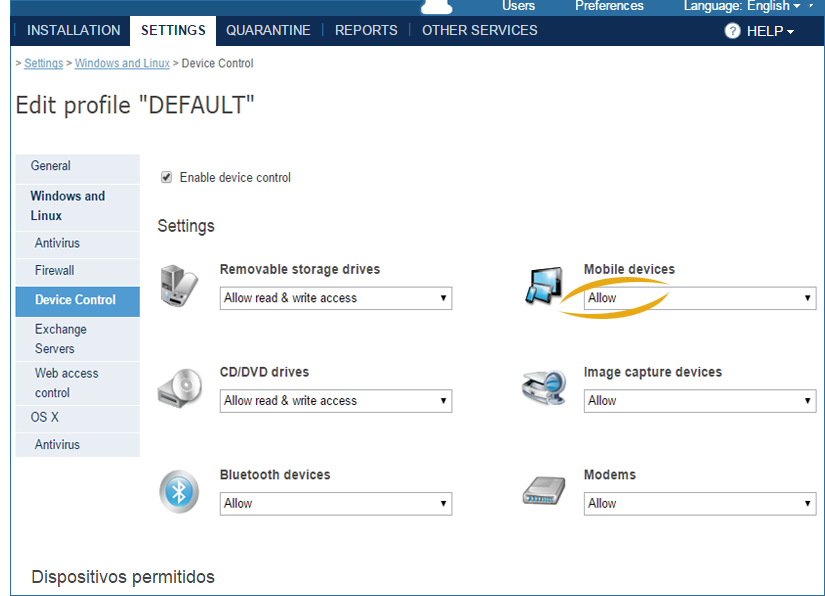
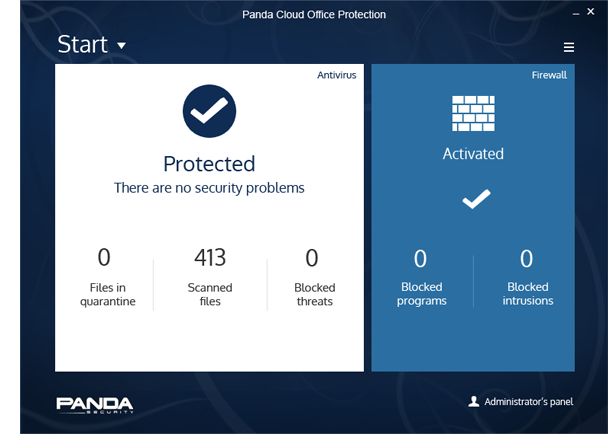
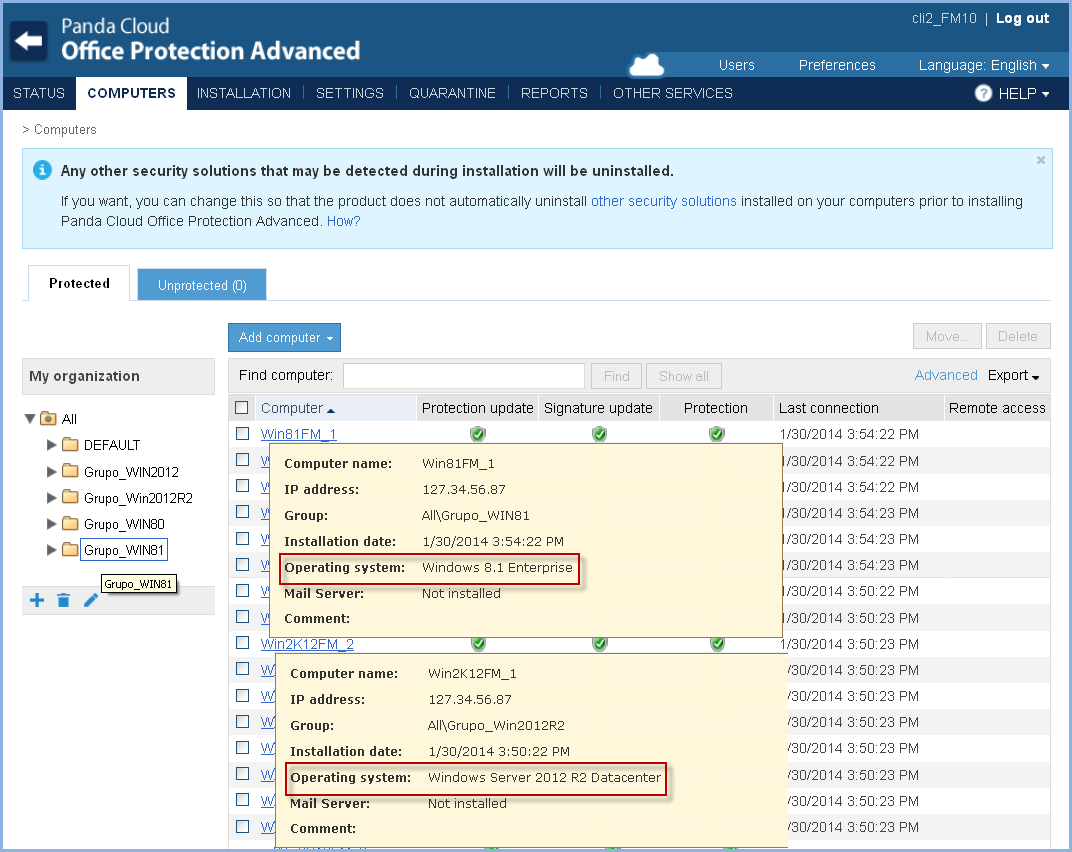
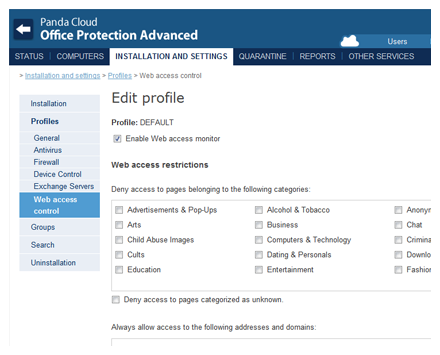
Web access control
Panda Cloud Office Protection Advanced now lets you monitor and control websites visited and block unproductive and/or dangerous websites for your company.
All without the need to install 'heavy' browser bars that slow down Web browsing regardless of the browser used.
Protection for Linux
Run on-demand and scheduled scans on Linux computers (SUSE, RedHat, Ubuntu and Debian), just like you do on Windows.
Even more protection
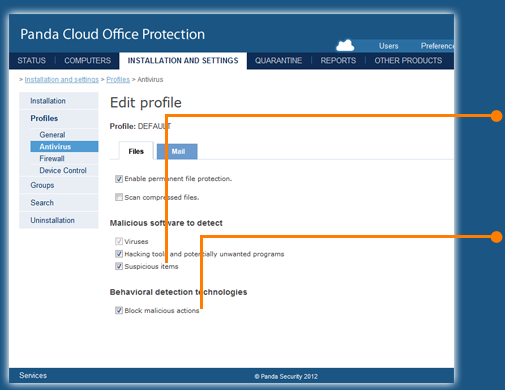
The new anti-exploit technology detects and neutralizes malware like Blackhole or Redkit that exploits zero-day vulnerabilities (in Java, Adobe, MS Office, etc.), before it infects the computer.
And, to keep things simple, this technology integrates seamlessly with Panda Cloud Office Protection's antivirus protection.
New update settings
Select the perfect time to update your protection with the new update settings.
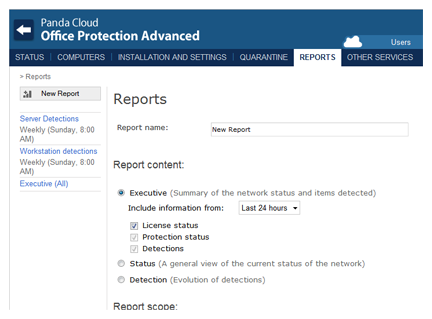
Reports where and how you want them
Save your favorite reports so you can run them at a later time without having to set up all the filters again. Schedule reports to run periodically and have them automatically sent out via email to specific recipients.