Endpoint Protection 7.20
New brand identity
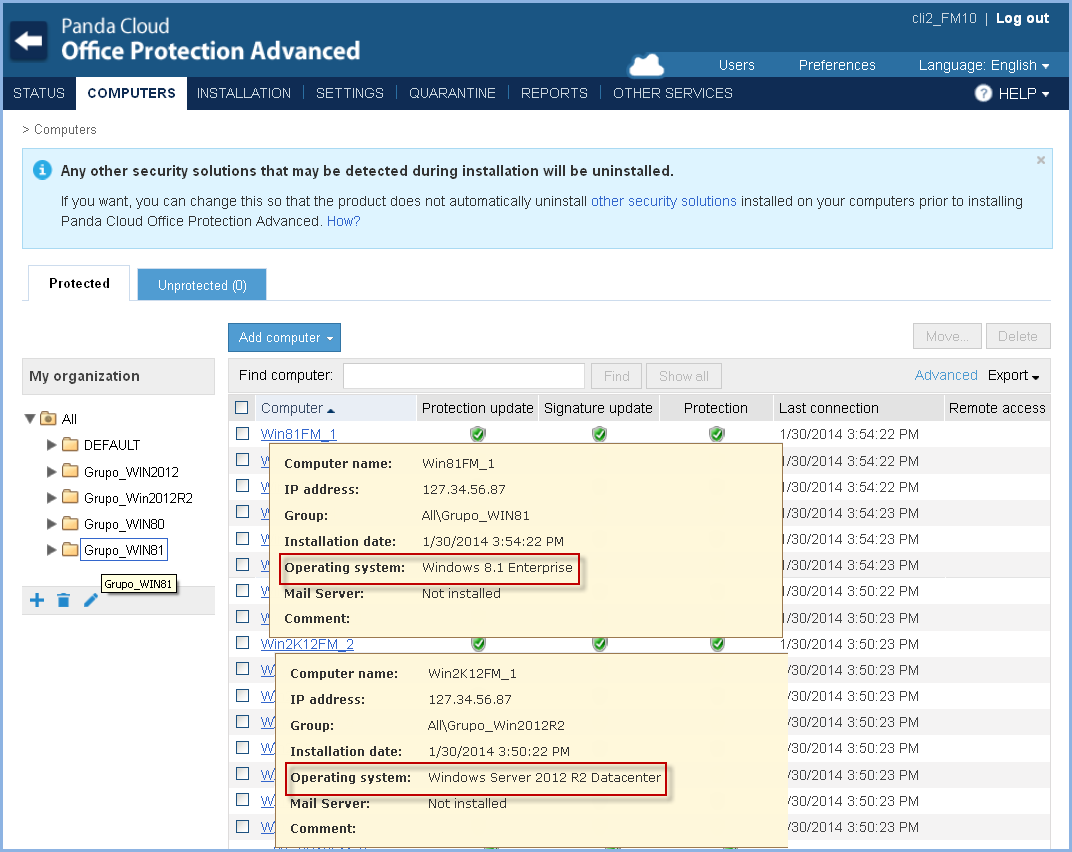
Panda Cloud Office Protection is now called Panda Endpoint Protection (Panda Endpoint Protection Plus in the case of the Advanced version). Additionally, the look and feel of the consoles has also been changed (new colors, fonts, images, etc.) to better reflect Panda's new brand identity.

Protection for Android
Protect your Android systems just as easily as any other device in your organization.
Panda Endpoint Protection Plus provides antivirus as well as anti-theft protection for your Android devices (Remote Lock, Remote Wipe, Geo-Location and Snap the Thief).
New user identification system
From now on, users will have to identify themselves through our IdP (Identity Provider) platform to access our consoles.
This represents a significant improvement in terms of security and user experience, and changes the way we create user credentials, allowing users to change their passwords, validating their email addresses, etc.
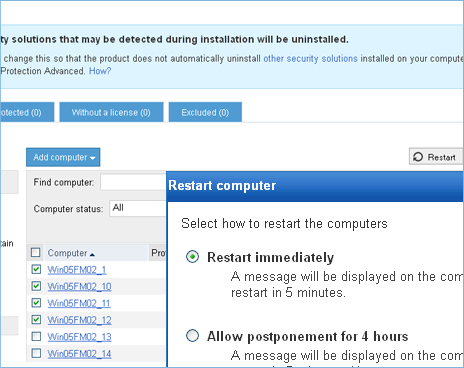
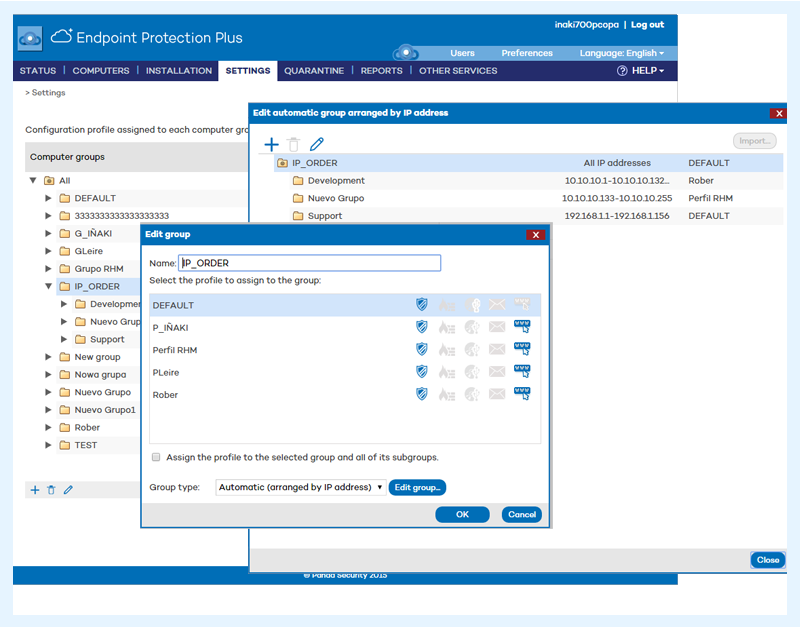
Automatic distribution of computers into groups by IP address
This version adds the ability to set rules to automatically distribute computers into groups and assign a configuration profile to them based on their IP addresses.
New protection engine
The protection engine has been updated with the latest technologies and improvements developed by Panda.