Adaptive Defense 360 2.4.1

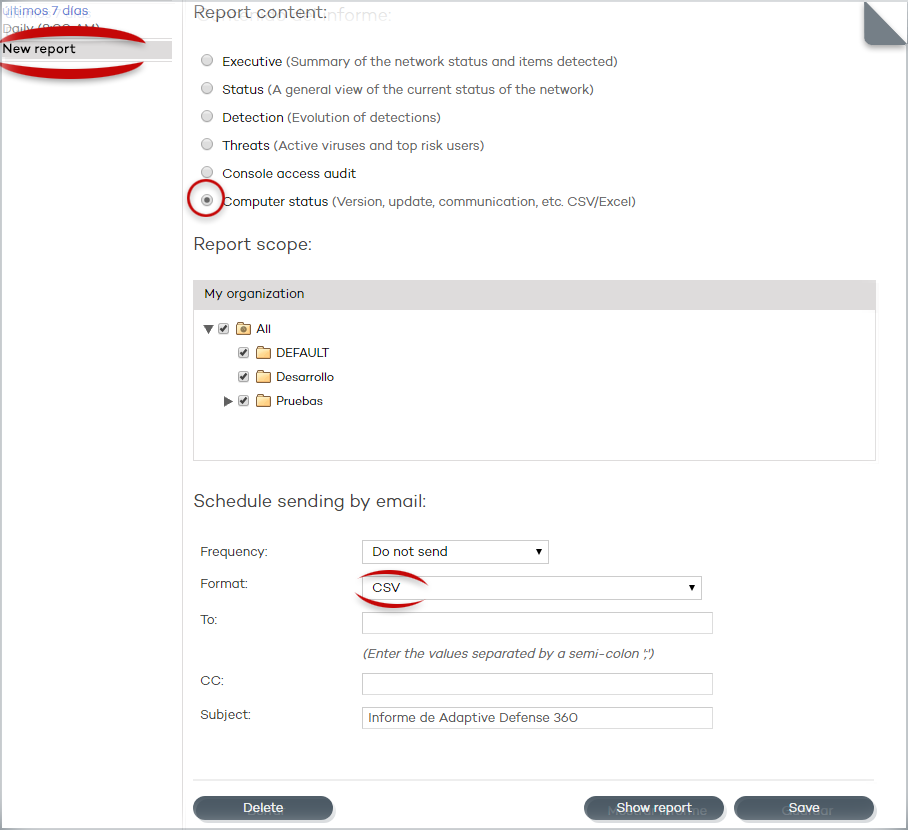
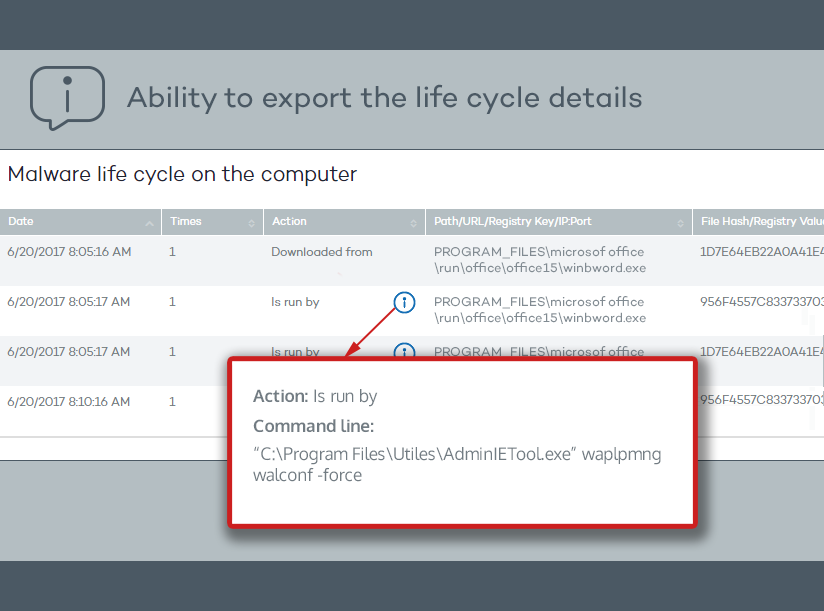
Ability to export the life cycle details
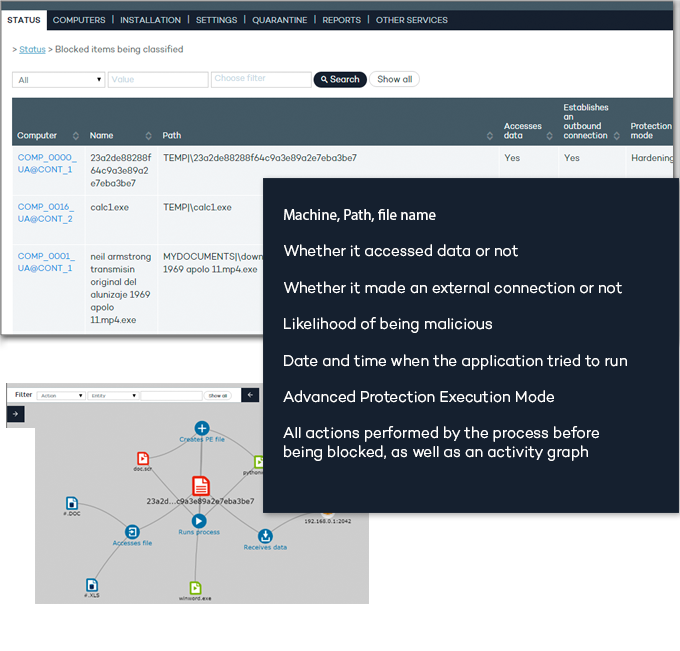
of one or multiple detections as well as command-line parameter information
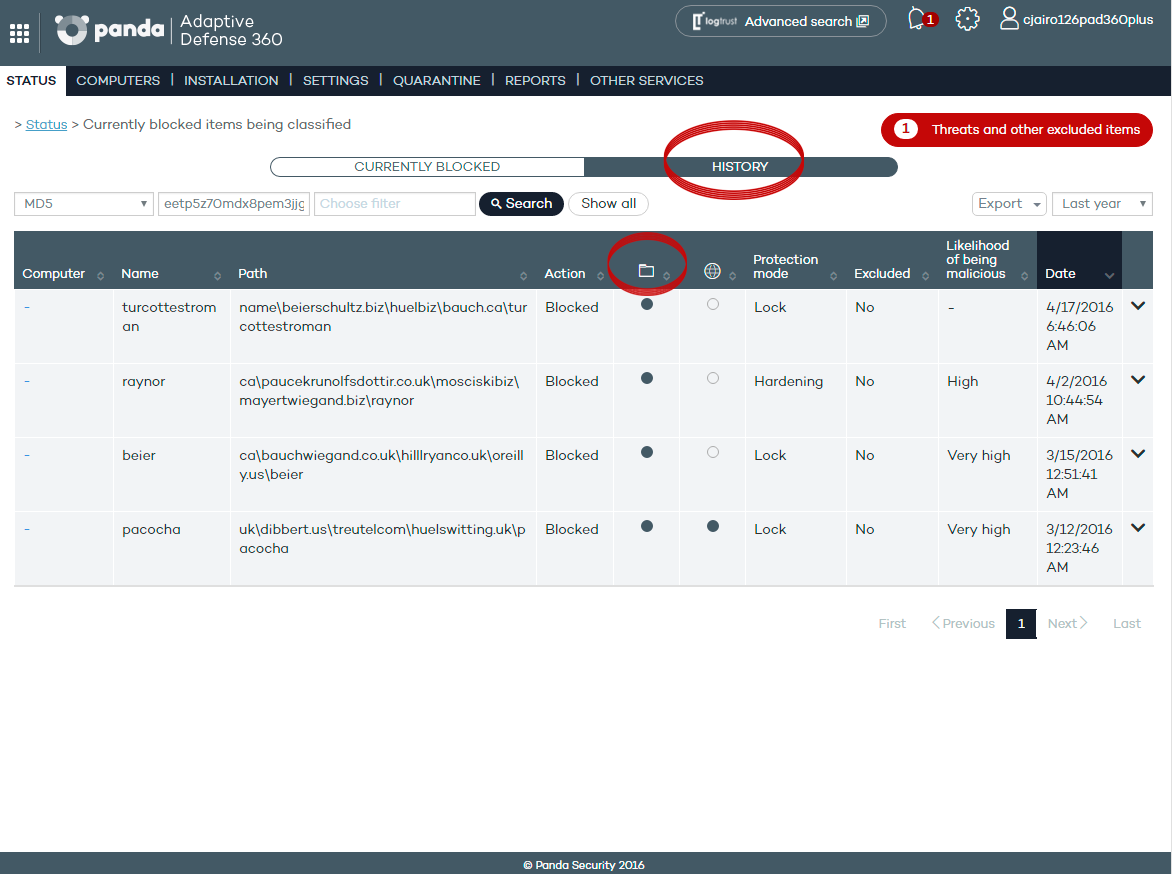
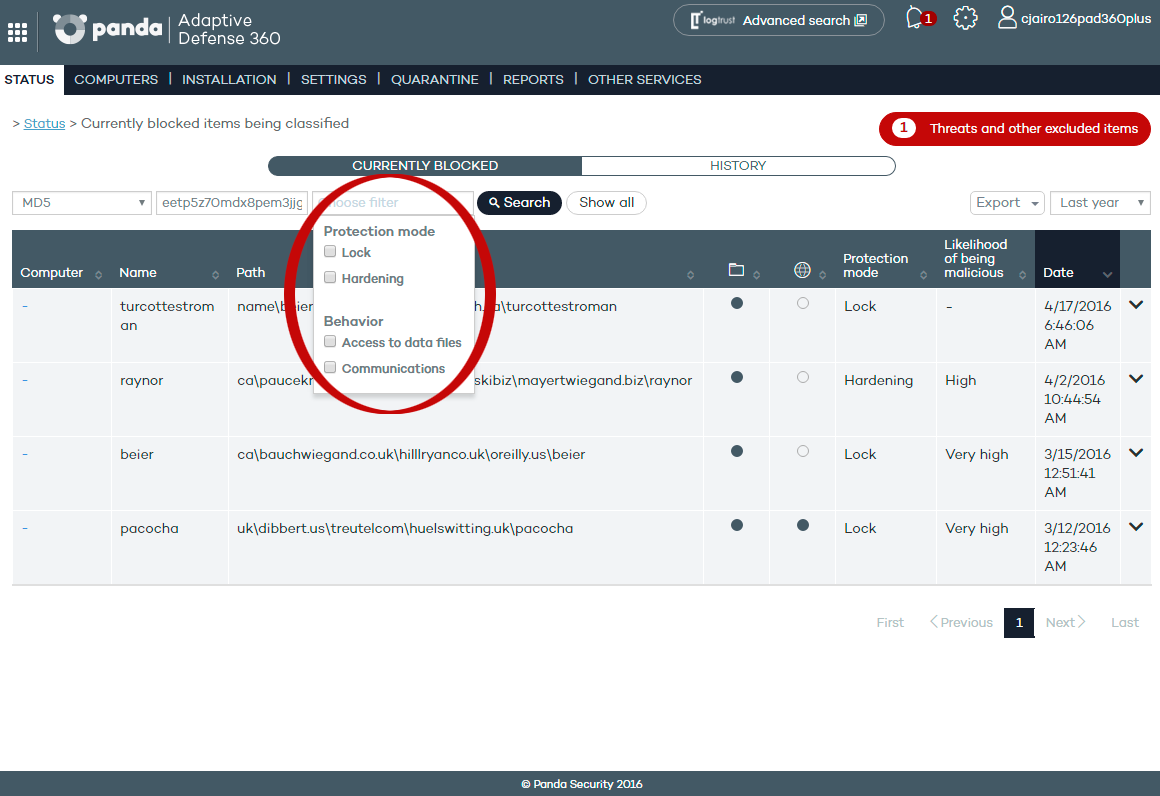
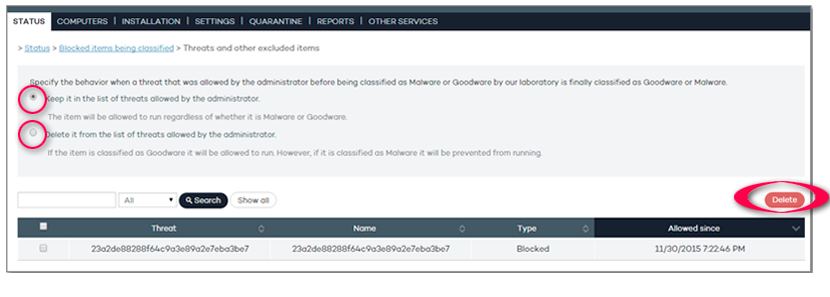
This version provides the ability to export the life cycle details of one or multiple detections (or blocked items) to CSV format.
Also, the console will display information about the command-line parameters used by attackers employing PowerShell scripts.
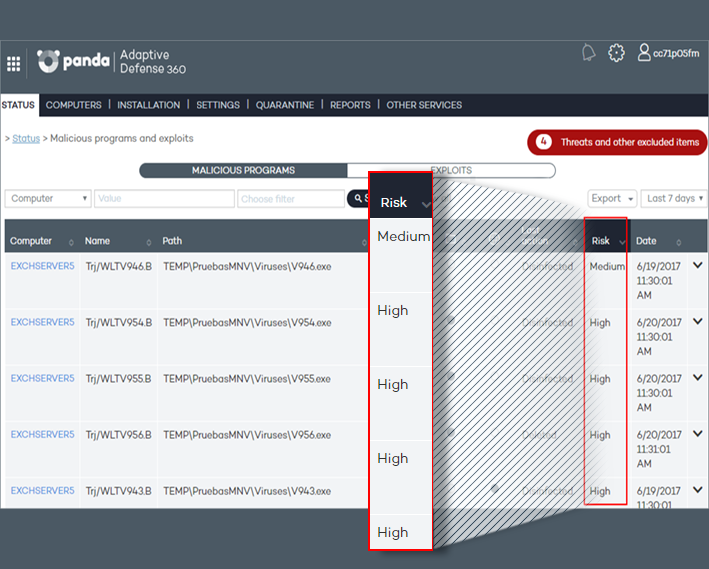
Prioritization of incident analysis
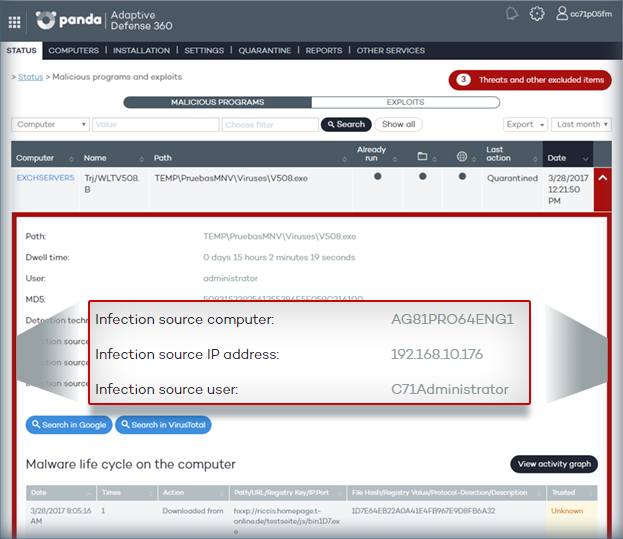
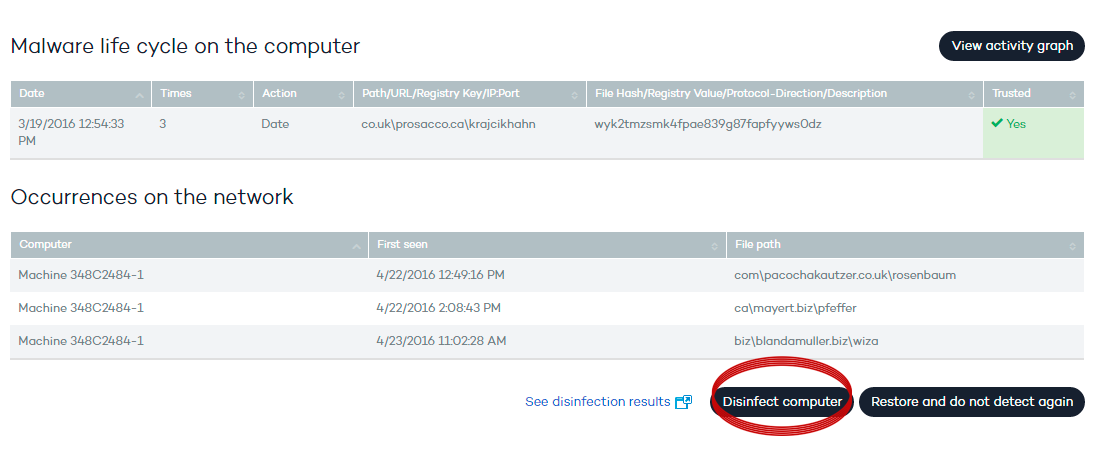
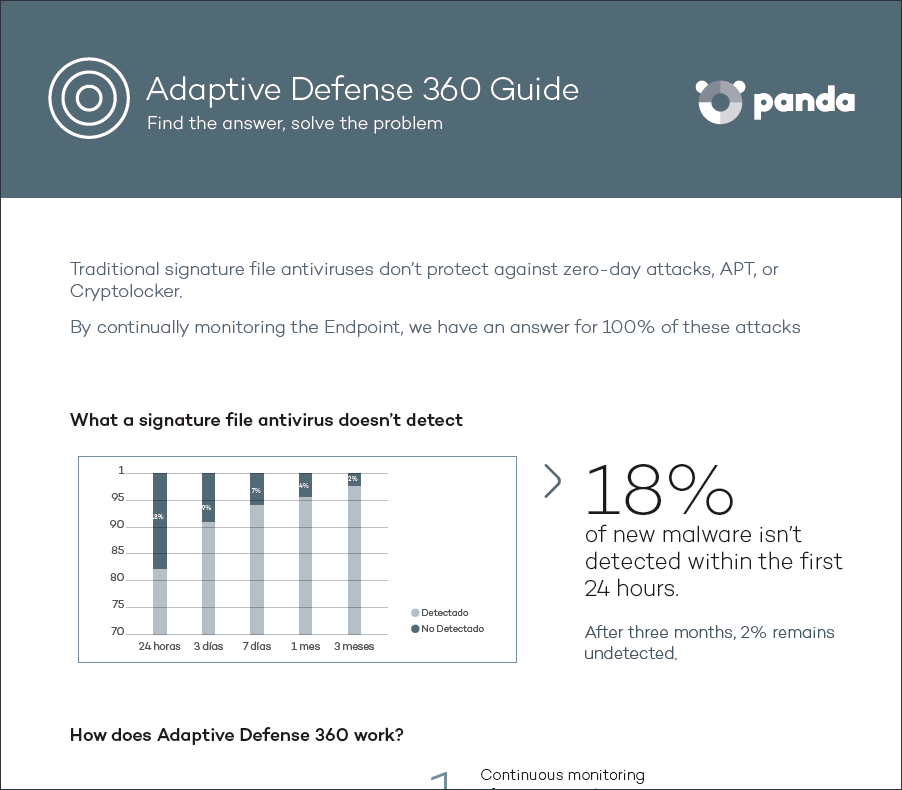
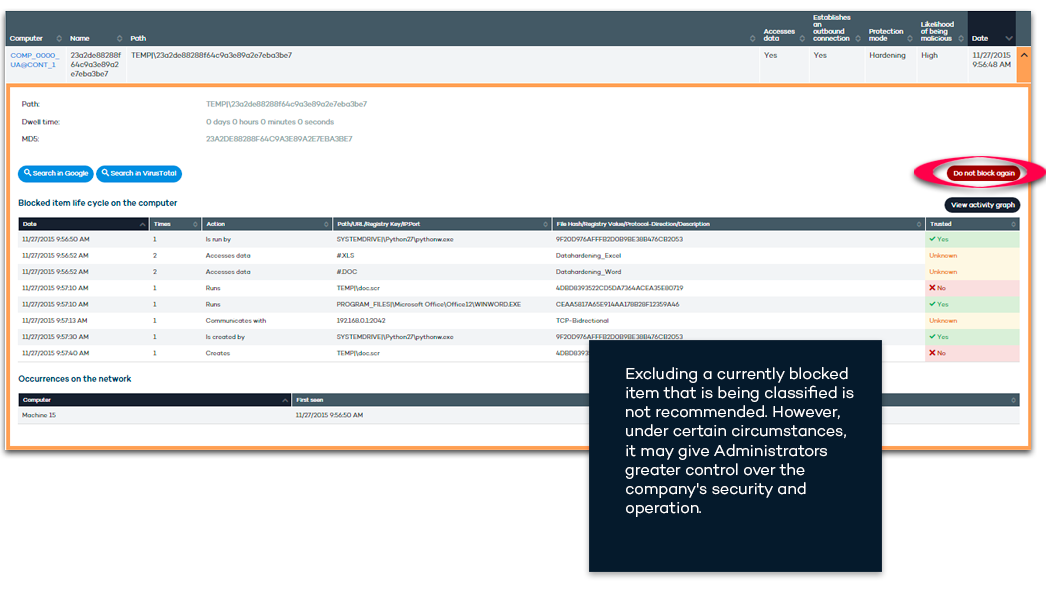
Prioritization of incident analysis (origin, impact, etc.) in the detection of malware or PUP through the Risk indicator.
- The risk is high when the malware or PUP was run before it was detected and has accessed files and/or established Internet connection.
- The risk is medium when the malware or PUP was run before it was detected but didn’t access any file and didn’t establish any Internet connection.
- The risk is low when the malware or PUP was not executed before being detected.
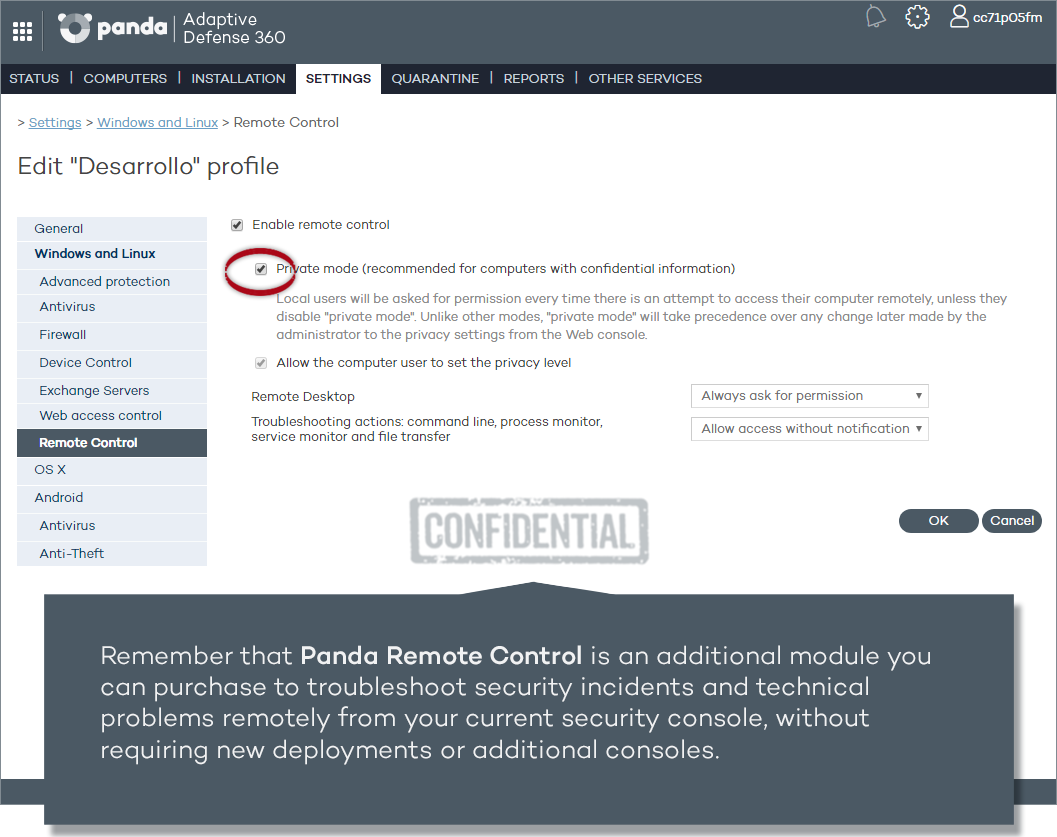
New private mode in Panda Remote Control
This new version of Panda Remote Control incorporates a new privacy level: private mode.
This mode, recommended for computers with confidential information, ensures that every time there is an attempt to access a computer remotely, the computer user is asked to allow or deny the action.
Unlike other modes, "private mode" will take precedence over any change later made by the administrator to the privacy settings from the Web console.
Only end users will be able to disable "private mode" if enabled.